SOC 2 (Service Organization Control 2) is a compliance framework developed by the AICPA (American Institute of Certified Public Accountants) to ensure that service providers securely manage customer data.
SOC 2 focuses on five key Trust Service Criteria:
- Security – Protection of systems and data against unauthorized access.
- Availability – Ensuring systems are operational and available as agreed.
- Processing Integrity – Ensuring accurate and reliable data processing.
- Confidentiality – Protecting sensitive business or customer data.
- Privacy – Handling personal data according to privacy principles.
¶ 2. Why is SOC 2 Important?
- Builds trust with customers and partners.
- Helps meet security requirements in contracts.
- Reduces the risk of data breaches.
- Enhances compliance with other security standards (ISO 27001, GDPR, etc.).
¶ 3. Compliance and security best practices for AWS
¶ 3.1. Network segmentation
Network segmentation is crucial to isolating critical assets and preventing unauthorized access. AWS provides multiple tools and services to achieve logical network separation using VPCs, Subnets, Security groups, AWS Network Firewall, and VPC Peering.
Network Segmentation Best Practices in AWS:
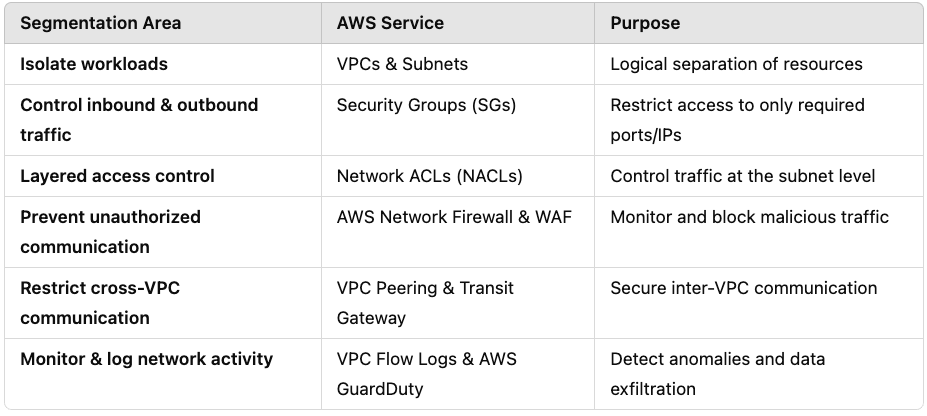
Network Segmentation in AWS can be implemented through following steps:
- AWS VPCs: Logical isolation of workloads.
- Subnets & Route Tables: Segregate internal/external traffic.
- Security Groups: Control inbound/outbound traffic. AWS Security Groups act as virtual firewalls to control inbound and outbound traffic for EC2 instances, RDS databases, EKS and other AWS resources.
- VPC Peering connections & NAT Transit Gateway: Secure inter-VPC communication.
Network isolation can be demonstrated through network architecture diagrams showing segmentation AWS VPCs. You can visualize your network using AWS Cloud Workloads
¶ 3.2. Preventing Unauthorized Data Exfiltration
Unauthorized data exfiltration occurs when sensitive data is transferred out of your AWS environment without proper authorization. AWS provides multiple security controls to prevent and detect data leaks:
✅ Restrict Internet Access:
- Block EC2 outbound access Security Groups: AWS Security Groups (SGs) operate at the instance level and provide fine-grained access control based on specific resources. Unlike NACLs, security groups allow rules to be applied dynamically, reducing the risk of unintended exposure.
- Enforce VPC Endpoints: Restrict S3 access to internal traffic.
✅ Monitor & Detect Unauthorized Transfers:
- Use VPC Flow Logs to track data transfers.
- Enable GuardDuty to detect unusual outbound requests.
- Scan S3 for sensitive data leaks using AWS Macie.
✅ Block Unauthorized API Calls & Access:
- Enforce Check S3 Bucket Policies:: AWS Console → S3 → Bucket Permissions (block public access).
- Use IAM SCPs to block cross-account data transfers.
- Use AWS Network Firewall: Prevent exfiltration via Layer 7 rules.
✅ Enforce Encryption & Secure Transfers:
- Enforce S3 encryption (SSE-S3, KMS).
- Require TLS 1.2 for all data transfers.
¶ 4. Compliance Responsibility management
For SOC 2 compliance client is responsible for securing and managing overall infrastructure, access controls, and applications, while CTO2B ensures the availability, security, and compliance of the managed platform. Compliance responsibilities are generally divided as follows:
- Identity & Access Control - client responsibility.
- Secure Code Deployment - client responsibility.
- VPCs, security groups - CTO2B responsibility.
- AWS Network Firewall - client responsibility.
- AWS CloudTrail, GuardDuty, and VPC Flow Logs - client responsibility.
- Kubernetes audit logging - CTO2B responsibility.
- Backup & Disaster Recovery - CTO2B responsibility.
- Cluster Control Plane Security - CTO2B responsibility.
- Networking & Isolation - shared responsibility.
- Monitoring & Logs - shared responsibility.
- Compliance & Governance - shared responsibility.
- Data Encryption - shared responsibility.
¶ 5. Provide required compliance Evidence
-
Configuration Baselines (AWS Config) - helps enforce and monitor security compliance. Go to AWS Console → AWS Config → Rules to enable predefined security rules (e.g., encryption, IAM policies, logging).
-
Terraform State Files (Track Infrastructure Changes) - confirms network segmentation and enforced S3 encryption & access control.
-
Change Management Logs (AWS CloudTrail & Config) - to track who changed what, use AWS CloudTrail, AWS Config.
-
AWS Security Hub (SOC2 Compliance Report) - Enable AWS Foundational Security Best Practices for SOC2 evidence.
✅ Go to AWS Console → Security Hub → Compliance Standards. Enable AWS Foundational Security Best Practices for SOC2 evidence.
✅ Download Security Hub Report.