¶ Developer Database Access
CTO2B makes it easy to securely access remote MySQL or PostgreSQL databases running in your Kubernetes environment using port-forwarding and environment-aware connection details. This is useful for local development, debugging, or performing manual queries without exposing your databases publicly.
The same steps apply regardless of the database engine (MySQL or PostgreSQL).
Before connecting:
- Ensure you have access to CTO2B and are logged in.
- Install the following tools locally:
- kubectl
- Teleport CLI (tsh)
- A local database client
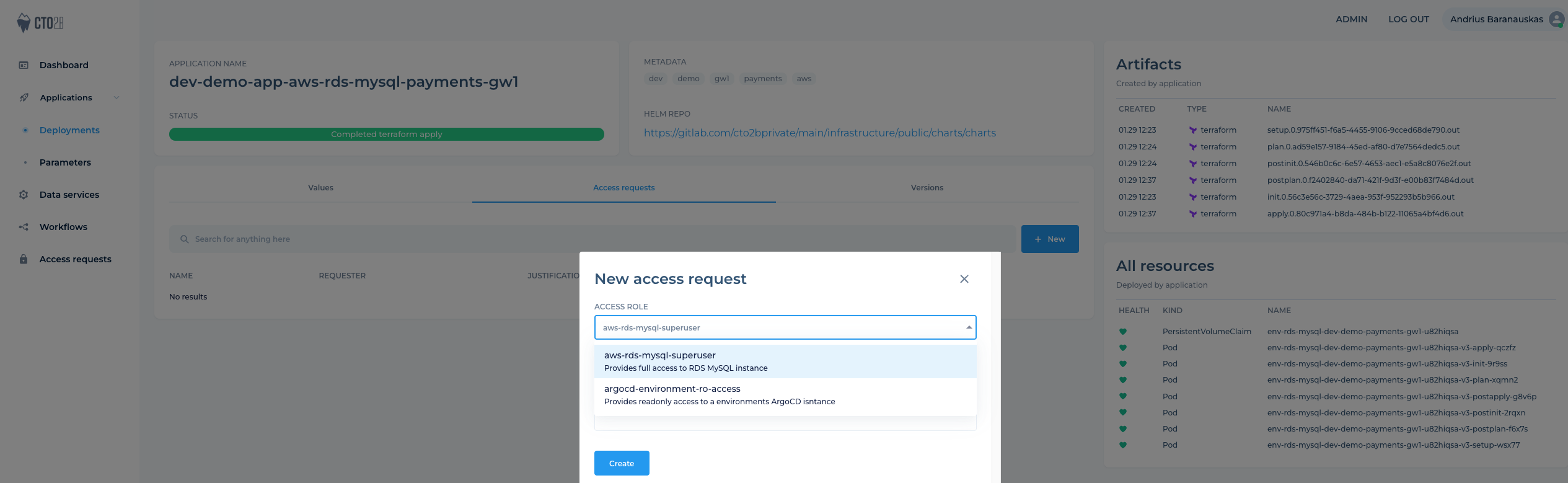
¶ Request access
- Navigate to your Database instance in Sview UI and pre
Access Requeststab , select database role and pressCreate
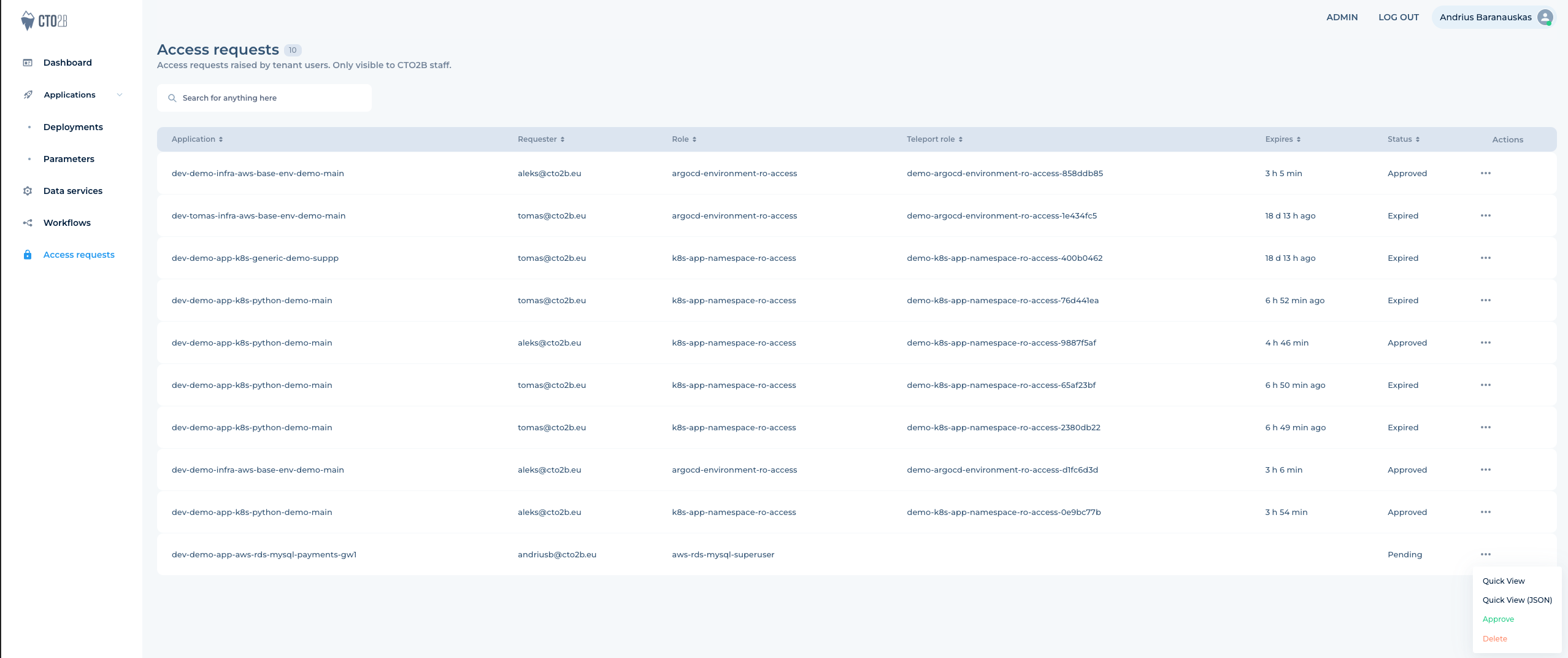
¶ Approve access
- Get your access request approved. Your teammate with
Approvalrole or CTO2B support can approve requests via Slack Approval bot or UI:
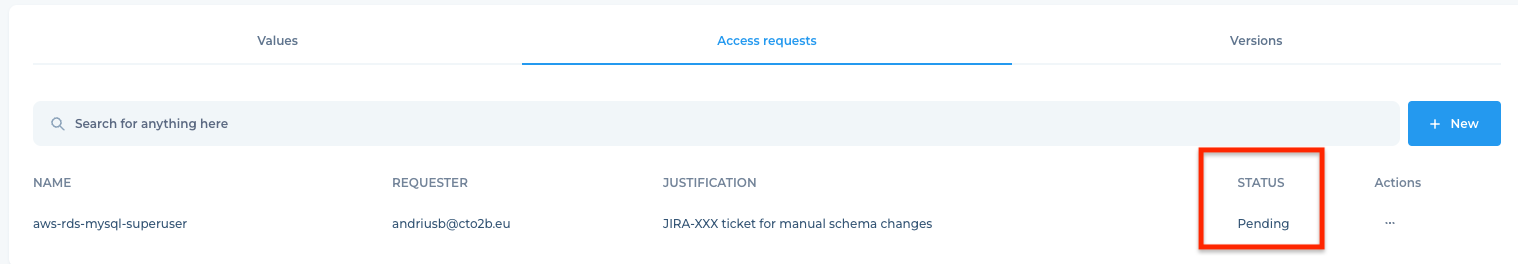
Once approved you shoudl see status change from Pending to Approved
¶ Access Teleport
- Login to CTO2B Teleport via CLI tsh utility replace
--userargument with your username
NOTE: If you never logged in the CTO2B Teleport before, request via support slack
Temporary Credentials Cration Link
tsh login --user [email protected] --proxy https://teleport.manage.cto2b.eu
I have 2FA configured on Biometric key it requests code from a OTP device. It shows asigned my temporary access role demo-aws-rds-mysql-superuser-354314d3 that was approved
$ tsh login --user [email protected] --proxy https://teleport.manage.cto2b.eu
Enter password for Teleport user [email protected]:
Tap any security key or enter a code from a OTP device
> Profile URL: https://teleport.manage.cto2b.eu:443
Logged in as: [email protected]
Cluster: teleport.manage.cto2b.eu
Roles: access, demo-aws-rds-mysql-superuser-354314d3
Logins: andrius
Kubernetes: enabled
Kubernetes groups: system:masters
Valid until: 2024-01-30 03:01:27 +0200 EET [valid for 12h0m0s]
Extensions: login-ip, permit-agent-forwarding, permit-port-forwarding, permit-pty, private-key-policy
Did you know? Teleport Connect offers the power of tsh in a desktop app.
Learn more at https://goteleport.com/docs/connect-your-client/teleport-connect/
¶ List instances
- List databases you can access
$ tsh db ls
Name Description Allowed Users Labels Connect
----------------------------- ---------------------------- -------------------- ------------------------------------------------------------------------------------------------------------------- -------
dev-demo-payme-gw1-rds-mys RDS instance in eu-central-1 [superuser teleport] Capability=rds-mysql,Environment=demo,Instance=gw1,Namescpace=payments,Stage=dev,Terraform=true,account-id=94862...
¶ DB Shell Access
- Access your database in shell
tsh db connect --db-user teleport <db-instance-you-need-access-to>
# PSQL
tsh db connect --db-name app_test --db-user teleport dev-demo-test-rds-postgres
#Mysql
tsh db connect --db-user teleport dev-demo-payme-gw1-rds-mys
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 10008
Server version: 8.0.34 Source distribution
Copyright (c) 2000, 2023, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> CREATE DATABASE demo;
Query OK, 1 row affected (0.11 sec)
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| demo |
| information_schema |
| mysql |
| performance_schema |
| sys |
+--------------------+
5 rows in set (0.11 sec)
NOTE: for Google GCP CloudSQL instances provide full name
--db-user teleport-agent-sa@<GCP project ID>.iam
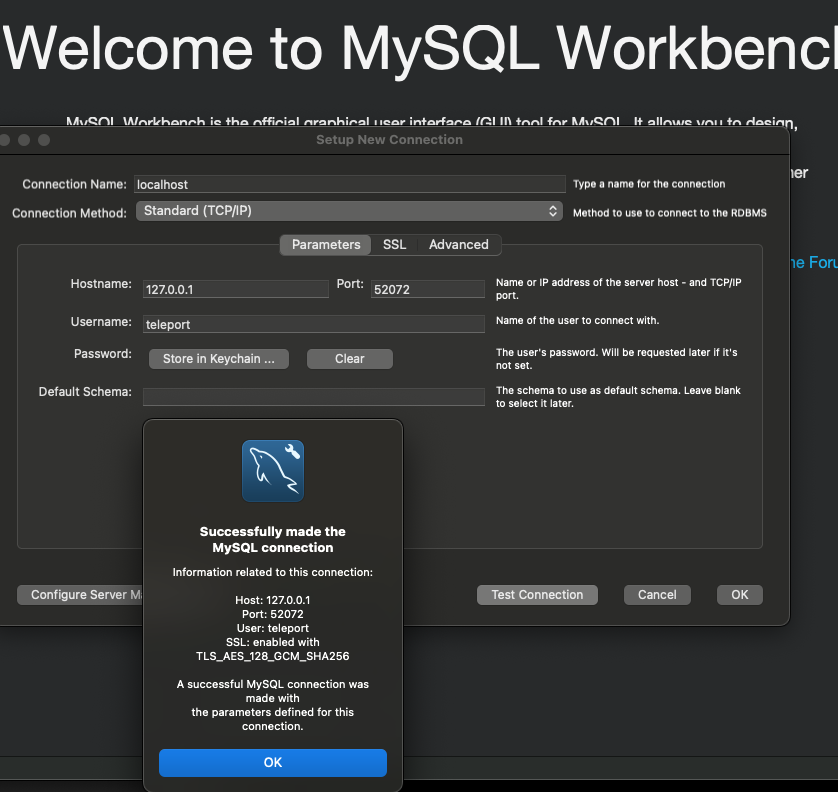
¶ DB WorkBench Access
- Access in WorkBench
Open port forward tunnel and keep this command hanging
tsh proxy db --tunnel --db-name mysql --db-user teleport dev-demo-payme-gw1-rds-mys
$ tsh proxy db --tunnel --db-name mysql --db-user teleport dev-demo-payme-gw1-rds-mys
Started authenticated tunnel for the MySQL database "dev-demo-payme-gw1-rds-mys-eu-central-1-948620892373" in cluster "teleport.manage.cto2b.eu" on 127.0.0.1:52072.
To avoid port randomization, you can choose the listening port using the --port flag.
Teleport Connect is a desktop app that can manage database proxies for you.
Learn more at https://goteleport.com/docs/connect-your-client/teleport-connect/#connecting-to-a-database
Use the following command to connect to the database or to the address above using other database GUI/CLI clients:
$ mysql --user teleport --database mysql --port 52072 --host localhost --protocol TCP
Note the random generated port is assigned for your connection if you expect same port every time you can add --port 13306 flag as example.